
My illustration sketch of a CypherPunk (数码朋克) in action, performing a coup d’état, inspired by the ‘Crypto Anarchist Manifesto’. Of course, championing Anonymous (匿名者), he is wearing the Guy Fawkes mask. V for Vendetta.
———————————————————-
Almost 20 years ago, Timothy C. May published to the Cypherpunks Mailing List a short text espousing the role of computer technology in forging new means for individuals to communicate and transact.
In the 90s, the cypherpunks (a group of which May way a founding member) were at the front lines of a battle with intelligence agencies.
At the heart of the conflict lay encryption – the advent of public-key cryptography made obfuscation techniques (traditionally reserved to military organisations) easily accessible to individuals and businesses.
This development didn’t sit too well with the overlords, who unsuprisingly engaged in a campaign to weaken and limit its use.
‘You have a right to privacy, until we decide otherwise’
In 1993, the NSA announced the Clipper chip, every privacy activist’s dream – it would enable the communications of the public to remain encrypted.
The only catch? A backdoor that would ensure the government had unfettered access for surveillance purposes (because, you know, “national security”). The idea was that American hardware manufacturers would incorporate these chips into their products.
———————————————————-

The illustration showcases the words ‘CypherPunk’, ‘Anonymous Systems’, ‘Cryptography’, ‘Decentralization’ and ‘Crypto Anarchist Manifesto’.
———————————————————-
Running parallel to this debate was that of the export of cryptography from the United States. Until 1996, encryption technologies were classed as munitions — Phil Zimmerman, creator of PGP, was subject to a criminal investigation for publishing his seminal creation online (this was later dropped).
The coordinated efforts of the cypherpunks and industry figures in lobbying against the adoption of the chip saw the initiative fail (Matt Blaze published a paper in 1994 highlighting its technical vulnerabilites). By 1996, the Clipper was already a distant memory, and exports around cryptography were significantly relaxed.
The Battle Rages On
The work of the cypherpunks has been monumental in defending what many perceive to be fundamental rights in cyberspace. Central to the ideas discussed in The Crypto Anarchist Manifesto is the harnessing of things like zero-knowledge proofs, public-key cryptography and various other protocols so that individuals can pseudonymously interact with each other and evade censorship, whilst promoting free markets, free speech and privacy.
Cryptography is perhaps one of the most powerful weapons for peacefully protecting the integrity of one’s activities from adversaries. Digital identities, stateless virtual currencies and free markets are the building blocks for a more anarchic cyberspace, characterised by self-sovereignty and unstoppable interactions between anonymous individuals.
In my own fight to promote decentralization, I founded Crypto Chain University back in 2010, to compile blockchain and cryptocurrency research papers, and making it open-source, free-for-all to tap into the knowledge base.
———————————————————-
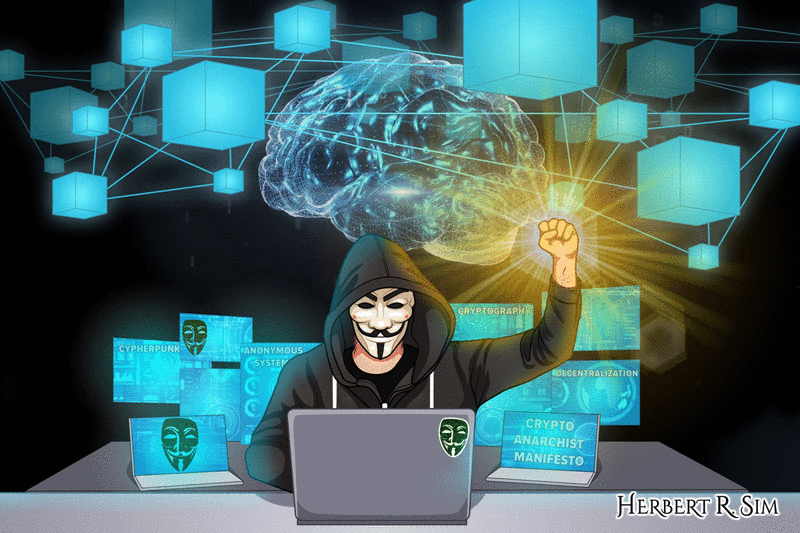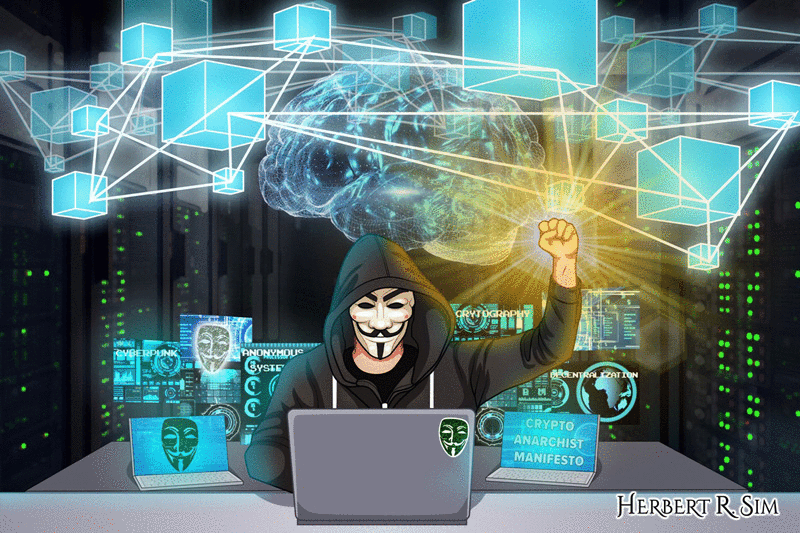
In my illustration it showcases the CypherPunk with his fist clenched in euphoric punch of declaring Victory.
———————————————————-
The Crypto Anarchist Manifesto
Written by Timothy C. May on 22 Nov 1992.
A specter is haunting the modern world, the specter of crypto anarchy.
Computer technology is on the verge of providing the ability for individuals and groups to communicate and interact with each other in a totally anonymous manner. Two persons may exchange messages, conduct business, and negotiate electronic contracts without ever knowing the True Name, or legal identity, of the other. Interactions over networks will be untraceable, via extensive re- routing of encrypted packets and tamper-proof boxes which implement cryptographic protocols with nearly perfect assurance against any tampering. Reputations will be of central importance, far more important in dealings than even the credit ratings of today. These developments will alter completely the nature of government regulation, the ability to tax and control economic interactions, the ability to keep information secret, and will even alter the nature of trust and reputation.
The technology for this revolution–and it surely will be both a social and economic revolution–has existed in theory for the past decade. The methods are based upon public-key encryption, zero-knowledge interactive proof systems, and various software protocols for interaction, authentication, and verification. The focus has until now been on academic conferences in Europe and the U.S., conferences monitored closely by the National Security Agency. But only recently have computer networks and personal computers attained sufficient speed to make the ideas practically realizable. And the next ten years will bring enough additional speed to make the ideas economically feasible and essentially unstoppable. High-speed networks, ISDN, tamper-proof boxes, smart cards, satellites, Ku-band transmitters, multi-MIPS personal computers, and encryption chips now under development will be some of the enabling technologies.
The State will of course try to slow or halt the spread of this technology, citing national security concerns, use of the technology by drug dealers and tax evaders, and fears of societal disintegration. Many of these concerns will be valid; crypto anarchy will allow national secrets to be trade freely and will allow illicit and stolen materials to be traded. An anonymous computerized market will even make possible abhorrent markets for assassinations and extortion. Various criminal and foreign elements will be active users of CryptoNet. But this will not halt the spread of crypto anarchy.
Just as the technology of printing altered and reduced the power of medieval guilds and the social power structure, so too will cryptologic methods fundamentally alter the nature of corporations and of government interference in economic transactions. Combined with emerging information markets, crypto anarchy will create a liquid market for any and all material which can be put into words and pictures. And just as a seemingly minor invention like barbed wire made possible the fencing-off of vast ranches and farms, thus altering forever the concepts of land and property rights in the frontier West, so too will the seemingly minor discovery out of an arcane branch of mathematics come to be the wire clippers which dismantle the barbed wire around intellectual property.
Arise, you have nothing to lose but your barbed wire fences!
———————————————————-

